Web Applications (Basics)
Introduction
- A Web application refers to an application, which can be accessed through a Web browser, such as Internet Explorer or Mozilla Firefox.
- Web applications are those applications that are only accessible using Internet.
- Web applications came into existence to overcome the shortcomings of desktop applications which can be hosted on all the computers but not on the network or Internet.
- Web applications are generally hosted in client-server networking environment.
- The Web applications also help the companies in reaching out to prospective clients and conducting businesses online.
- The term ‘networking’ represents the processes involved in developing, designing, implementing, managing and upgrading network technologies.
- A network generally consists of two or more computers which are interconnected either logically or physically using special software and hardware.
- Networked computers exchange information and share resources.
- Networked computers generally involve different technologies, protocols and hardware devices to ensure connectivity and communication.
- Networking provides the following benefits to its users:
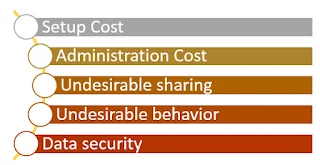
- Despite so many advantages, networking also involves some challenges and risks as listed below:
Components of Network
- A network usually comprises five basic components – server, client, channels, operating system and interface.
- Servers are powerful host computers that store data and execute applications.
- Clients are computers connected to the server that use the network and shared resources.
- Channels are circuits or pathways connecting networks through which different interconnected computers share the information.
- Network operating system is the operating system software on the server.
- Interface devices connect server and clients.
- The following figure shows a typical example of a network:
Types of Network
- On the basis of geography, networks are classified as follows:
- Local Area Network (LAN): LAN is a localized network. This type of network is useful when you want to connect two different departments in a building. The data transfer rate for LAN technologies is up to 1000 Mbps. LAN is a high-speed and fault-tolerant data network.
- The following are the characteristics of LAN:
- LAN helps in resource sharing, for example, data, software and hardware.
- It transfers data at a high speed.
- LAN’s reach is limited.
- LAN technology is generally less expensive than MAN and WAN.
- Metropolitan Area Network (MAN): MAN is a bigger version of LAN. MAN covers a larger area than LAN, but smaller than WAN. MAN generally connects two or more LANs or Campus Area Networks (CANs), for example, providing Internet services to users in a city. Typically, a MAN covers an area between 10 km and 100 km.
- The following are the characteristics and purpose of MAN:
- MAN covers a larger area than LAN.
- It covers a distance between 10 km and 100 km.
- It operates at a speed of 34 Mbps to 155 Mbps.
- Expensive equipment is required for forming a MAN.
- Wide Area Network (WAN): WAN is a type of network used to cover a wide geographical area or region. It links different metropolitan cities, countries and national boundaries. It may be located entirely within a state or country, or it may be interconnected around the world. The transfer rate of WAN is up to 155 Mbps or less as it often uses public telephone networks or leased transmission lines.
- The following are the characteristics of WAN:
- WAN exists in an unlimited geographical area.
- It is very susceptible to errors due to the distances involved.
- On the basis of component role, networks are classified as follows:
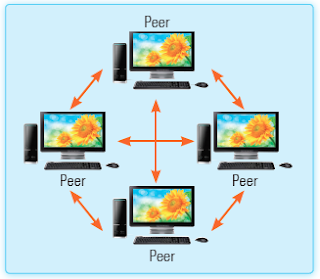
- Peer-to-peer network: In this type of network, all the connected computers are equal. In other words, each computer maintains its information and can serve both as a server as well as a client whenever required. Such network is primarily used in small companies or homes. A peer-to-peer network can have a maximum number of 10 peers at a time.
- A peer-to-peer network is shown in the given figure.
- Server-based network: This type of network provides greater security and centralized control where a dedicated server controls all the network operations. The following figure shows a server-based network:
- Client-based network: This is a more refined server-based network which employs the processing power of a client workstation to execute some functions locally and requesting further processing from the server. This increases the overall processing speed. The following figure shows a client-based network.
Network Topology
- Network topology refers to the basic geometric layout according to which the server and clients are connected via a channel.
- Different topologies provide different levels of access to the clients through the channel.
- The three most common network topologies are bus, ring and star, as shown in given figures.
Network Protocols and OSI Model
- Communication and information exchange over a network takes place at different levels.
- The Open Systems Interconnection (OSI) reference model or the OSI model is used as a fundamental framework to classify and regulate the processes involved with communication and message exchange over the network.
- It represents the sequence of processes by which a message is transferred from one computer to another on a network.
- According to OSI model, the services and functions of a network can be divided into discrete layers.
- Each layer provides some services to the upper layer.
- Following figure shows the services and protocol at different layers of the OSI model:
Internet
- Internet is defined as a worldwide network of computers connected to each other for sharing information.
- From searching for information to downloading music and videos, sending and receiving e-mail messages to communicate with friends and conducting everyday transactions, the Internet has become an integral part of our lives.
- The Internet has evolved as a fast and economically feasible mode of communication.
- Apart from this, it is one of the best sources of news and latest happenings around the world, which is being constantly updated in real time.
- The computers on the Internet are connected to each other with the help of various small networks. These different small networks are then connected to the Internet backbone using several gateways.
- Following figure is a diagrammatic representation of the working of the Internet:
Modem
- Modem is a device which is used to transmit data over a network.
- In a network, while computers are communicating, a computer from the sender’s side sends the data in binary code to a modem. The modem at the sender’s side converts the binary-coded data into analog signals. Then these signals travel along the telephone network. When the data reaches the destination computer, the modem connected to that computer converts the analog signals back into the binary-coded data, which can be read by the computer.
- Data transmitted through modem is measured in bits per second (bps). This measurement gives us the speed of the modem. We have modems with different speeds, for example, 256 Kbps, 512 Kbps, 2 Mbps and 8 Mbps.
- There are two types of modems:
- External modem: It refers to the modem that has to be connected to your computer as well as your telephone line with cables and electric socket.
- Internal modem: It is the modem which is built inside your computer.
Different Ways of Connecting to Internet
There are two main ways of connecting to the Internet, that is, wired and wireless.
- Wired Internet connections are:
- Dial-up Connection
- Broadband Connection
- Leased Line
- Wireless Internet connections are:
- Wireless Fidelity (Wi-Fi)
- Worldwide Interoperability for Microwave Access (WiMAX)
- 3G
- 4G
- 4.5G
- 5G
WWW
- World Wide Web (WWW), also known as Web in short, was developed by Tim Berners-Lee of the European Laboratory for Particle Physics (CERN) in Switzerland.
- WWW represents an information space where documents and other web resources reside.
- These documents are connected by hyperlinks and can be accessed by URIs using Internet.
- WWW makes up a large part of the Internet and consists of websites that have one or more Web pages.
Working with Accessibility Options
- The ease of using computer due to hardware/software or their combination by the impaired people is known as computer accessibility.
- Windows 7 generally provides some common accessibility features which can be categorized as:
- Accessibility features for visually impaired users: People with limited eyesight can benefit from features like text-to-speech, enlarged cursor and high-contrast themes.
- Accessibility features for low-hearing or deaf users: Features like closed-captioning help in visually conveying the information to deaf users. Mono audio systems can equally transmit left and right audio signals to both the earbuds so that people with limited hearing do not miss any part of the audio.
- Accessibility features for limited mobility users: Keyboard shortcuts and sticky keys help people with limited mobility in effectively using the computer.
- The Accessibility features of Windows 7 are available via Ease of Access Center.
- Instant messaging refers to the real-time, text-based communication between people over the internet using instant messaging software.
- In case of instant messaging, a text message instantly appears on the screen of the receiver as soon as it is sent by the sender, hence the name.
- With instant messaging, people can share digital data in the form of text, video or audio. People can instantly engage with multiple users on a network.
- The various types of instant messaging app are as follows:
- Google Hangouts
- Adium
- Spark
- Jabber
- Yahoo messenger
- Skype
- For using instant messaging services, users need to install an instant messaging software application. The software program enables a computer with an IM client to use instant messaging features.
- The user has to register on the IM client (IM software) with a unique password and username combination.
- Once a user logs in with the correct credentials, the connection information such as port number and IP address of the user are sent to the IM server.
- The server checks the list of contacts of the client to see if any of them is also logged in and available for communication. Following figure shows an instant messaging model.
- In case the server finds an online connection, it sends the information back to the client. Also, the server sends the information about the client to the online contact.
- The information exchange allows both the users to communicate with each other either directly or via server.
- In most cases, IM systems work in client-server architecture for sending and receiving messages and other IM operations. In this case, all the messages exchanged between users are directed via the server. The IM server appears a single entity to a connected client but it can be a group of servers operated by the service provider or collective servers from independent service providers. In this model, when a user wants to communicate with another user, both must connect to the same IM service using their credentials.
- Some IM systems employ the peer-to-peer architecture, wherein they can directly share content or transfer files without the intervention of a central server. This architecture does not involve any file storage requirements. The network architecture only uses client’s bandwidth to transfer files.
- Peer-to-peer architecture is more scalable and cost-effective as compared to client-server architecture in case of instant messaging system.
- Instant messaging protocols are used by the IM clients and server for communicating with each other. These protocols include Extensible Messaging and Presence Protocol (XMPP) and Session Initiation Protocol for Instant Messaging and Presence Leveraging Extensions (SIMPLE).
- To ensure security, IM systems follow strict authentication. Authentication refers to the process of confirming and verifying the claimed identity of a user requesting connection to the IM system. Authentication serves as a security mechanism to provide authorized access to the system. Furthermore, users are granted appropriate permission for using specific IM system resources. The following figure depicts the authentication process followed by an IM system:
- Instant messaging provides notable benefits by offering a flexible mode of real-time communication in various sectors, such as business, education and social networking.
- Some applications of instant messaging are as follow:
- Voice over IP or VoIP Services: This service enables instant messaging users to talk to each other verbally by transmitting voice messages through the internet.
- Conferencing: Modern instant messaging software allows more than two people to talk to each other at a time, thereby providing a new mode of meeting over chat.
- Video Calls: People can talk to one another through real-time videos using instant messaging software.
- Video Conferencing: More than two people can participate on a video call in video conferencing. This helps in conducting meetings or learning sessions face-to-face even when the participants are physically present at different places.
- Job Outsourcing: Employers can find and employ overseas employees easily since instant messaging provides a safe, quick and cost-effective mode of instant communication with the remote employees.
- Google Talk was the iconic instant messenger software of Google which has been used to share text and voice. This iconic messenger software was discontinued by Google in June 2017 to be replaced by a revolutionary instant messenger software called Google Hangouts. It is available as a communication app in Gmail and can be used for conversations, discussions and sharing Google Drive documents. With Hangouts, you can easily chat with your friends or share media documents right from your Gmail account on your computer system or mobile device.
- A blog is a website or part of a website containing the thoughts and ideas of a user. It is written in the form of an online journal containing a continuous commentary on a specific subject. Other users can read the blog as well as post their comments on it.
- Generally, blogs contain textual information, but you can also share your
- photographs, videos and artworks with other users. The blogs can be of various types, some of which are as follows:
- Personal Blogs
- Corporate and Organizational Blogs
- Genre Blogs
- The given figure shows a WordPress.
- How will you get your web pages or blog up and running when your internet does not work? You may need to do it all over again if the connection goes out while working with an online blogging program. In such scenario, you can reduce some stress by using an offline blog editor.
- You do not require an active internet connection for writing web page content in an offline blog editor. Your blog post will be stored in your hard drive until you press the publish button in the editor.
- With offline editors, you can easily and automatically publish images and videos by merely hitting the publish button.
- An offline editor works on your computer system. Therefore, you can easily create web content without relying on the internet connection. You require the internet only for publishing the posts. With an offline editor, you can quickly publish multiple blogs at a time without logging in or out for every blog post.
- An offline blog editor lets you copy and paste content from other programs without adding extra code or useless font size and typefaces.
- Some commonly used offline blog editors used for editing blogs on Windows operating system are as follows:
- Qumana
- Windows Live Writer (Windows)
- BlogDesk (Windows)
- BlogJet (Windows)
- Have you ever done online shopping?
- Have you ever paid your bills using a mobile app?
- Both of these are examples of online transactions. In this manner, online transactions cover any monetary transactions made from a computer system or mobile.
- Online transactions help you in transferring funds easily to other accounts for making a payment.
- You can view all the recent transactions made online and can also get a printout of your bank account statement.
- You get a 24-hour access to your bank account with online transactions, popularly known as internet banking or online banking.
- You can control your online transactions from nearly anywhere, irrespective of your physical location. In this manner, online transactions provide a safe, flexible, convenient and fast mode of making payments electronically.
- You get two options to pay for the goods purchased online with your debit card – to make an offline payment via credit card processing or to make an online payment via electronic funds transfer.
- In an online transaction, the transfer of funds is completed via an EFT network to which your bank is associated.
- Payment processing takes place in two stages which include authorization for payment approval and settlement to transfer money to the receiver’s account.
- Internet was established to be an open, loosely connected network of computers to enable exchange of information and ideas. The data, internet transactions and communication over the web involve exchange of critical data over an insecure medium. Therefore, internet security is paramount.
- Internet security is extremely important for government agencies and business organizations to protect confidential details and critical financial data.
- The term ‘internet security’ includes browser security, authentication, data protection and security of data submitted via web forms.
- Various encryption mechanisms such as Pretty Good Privacy (PGP) are used to ensure secure data transfer over the internet.
- Resources such as Firewalls block unwanted traffic. Anti-virus, anti-malware and anti-spyware programs monitor and screen attachments for malwares or malicious data.
- Various security issues concern Internet users all over the world.
- The threats can be either undirected, which implies that they do not personally target your computer but may still affect its performance. For example, computer viruses and phishing emails are examples of undirected threats. You can protect yourself from such threats by implementing general security and ensuring secure browsing.
- You may encounter some directed threats that personally target your computer system or organization. Attackers use different techniques for directed threats which combine sophisticated tools with software engineering. You may counter such attacks by implementing basic security such as password protection and screen locks whenever you leave your computer unattended.
- Other circumstances that may potentially harm your system include:
- Malicious software
- Denial-of-Service Attack
- Phishing
- Application Vulnerability
- Computer users can effectively protect themselves from common security threats by using antivirus software, frequently backing up data and implementing measures to minimize risks of virus transmission.
- Users must protect their data with strong passwords and prevent identity thefts by sharing data only on secure websites and platforms.
- Computer users must adopt various security services via authentication, authorization, data integrity, access control, data confidentiality, DoS mitigation and auditing or logging.
- Some remedies for resolving internet security threats that may affect a computer system are as follows:
- Encryption: In this method data is encoded in a manner so that it can only be read by an authorized user. Encryption uses different algorithms at its core to generate ciphertext (encoded text) which can be read only after decryption.
- Digital Signature: The digital signatures help in authenticating the content by verifying the author, signature date and signature time.
- Firewall: A firewall serves as a barrier between the internet and LAN. It helps in minimizing the security risks by maintaining the confidentiality of the private resources.
- Antivirus Software: These are security programs for protecting a programmable device from security threats that work by detecting and eliminating malware and viruses.
- Password Manager: These software programs help in storing and organizing passwords. The passwords are stored in an encrypted format. The user must have a strong master password to access password database.
- Security Suits: These contain a collection of antivirus, firewalls and anti-spyware. They offer elaborated protection against theft and facilitate private internet browsing. They also provide other benefits, like safety check of portable storage devices, cloud anti-spam and file shredder.
* For any kind of query, kindly comment in the comment section.












Post a Comment